
Too-good-to-be-true investment offers are another classic scam on the dark web. Early participants may see some profit, but that money usually comes from new victims, not actual earnings. Eventually, the system collapses, and most people lose their entire investment. So, if a “business opportunity” sounds too perfect, it probably is. Once many users begin to rely on the site and store funds in escrow, the operators disappear, taking all the money with them and leaving their customers and clients with nothing.
Does The Darknet Still Exist?
On the other hand, it’s notorious for enabling illegal activity, including drug sales, weapons trafficking, counterfeit ID trading, hacking services, and the exchange of stolen personal data. Cybercriminals go on dark web marketplaces to buy and sell illicit goods and services. They engage in financial crime and sell other people’s stolen personal information, since they’re under the veil of anonymity. Just like on the regular internet, phishing is a big problem on the dark web as well. Fraudsters create fake versions of popular darknet sites to trick users into entering login details or personal data. If you fall for it and log in, they immediately steal your credentials and either sell or use them for other scams.
How Complex Are Dark Web Marketplaces Currently?
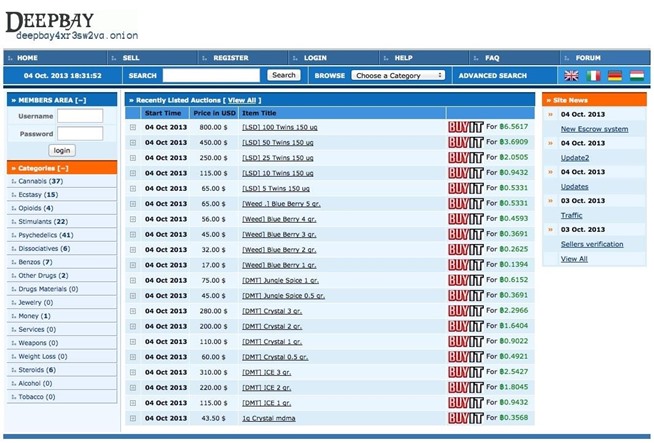
One thing that distinguishes BidenCash on the dark web, however, is how it markets itself. Darknet or dark web marketplaces are a hidden part of the internet that surface web users can’t access; they can only be accessed with special anonymity software called Tor. Many people (mostly criminals) use these sites to perform illegal transactions such as selling banned goods and services. The darknet is used for anonymous communication, accessing censored information, and protecting privacy.
How Is The Darknet Different From The Deep Web?
To reduce the risk of fraud, many dark markets offer escrow services. In this system, cryptocurrency is held by a trusted third party until the buyer receives the product or service as described. Once the buyer confirms satisfaction, the funds are released to the seller. Dark markets often employ end-to-end encryption for communication between buyers and sellers, enhancing security and privacy. This encryption ensures that messages cannot be intercepted and read by third parties, including law enforcement. The use of digital signatures can also help verify the authenticity of users and transactions.
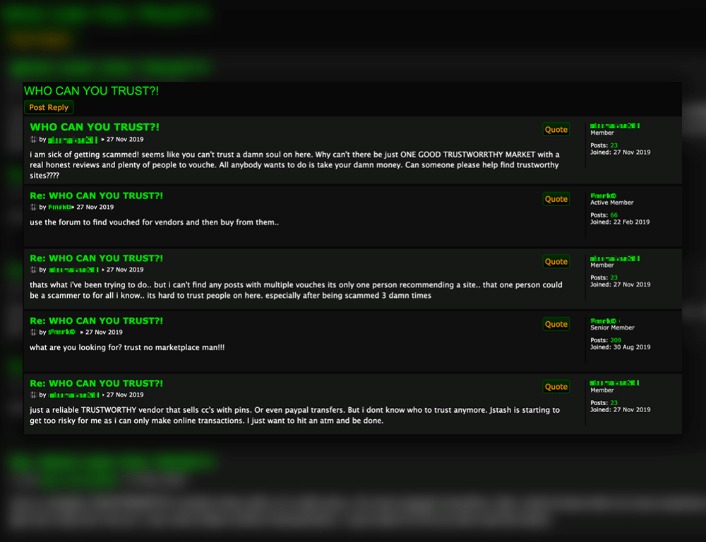
That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web. Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit. Some marketplace operators first build trust by running a legitimate platform. These hackers don’t hide in the shadows as much as you might think.
Personal Information
Darknets also serve as a platform for whistleblowers and privacy advocates. Platforms like SecureDrop enable individuals to submit documents and communicate securely with journalists, thereby exposing corruption and wrongdoings while preserving their anonymity. The significance is in safeguarding the right to free speech and the role of the press as watchdogs. Businesses should be aware of the potential for data leaks and invest in data loss prevention measures. With over 20 years of experience in cybersecurity and marketing, Ben has held leadership roles at companies like Check Point, Cognyte, Cylus, and Ionix.
- The UNODC (United Nations Office on Drugs and Crime) maintains that almost all firearms are originally manufactured through legal means.
- Further market diversification occurred in 2015, as did further developments around escrow and decentralization.
- Founded in 2014, BriansClub remains one of the oldest and most infamous dark web markets for stolen credit cards, fullz (complete identity kits), and dumps.
- After that, many other marketplaces kept trying to take its place and become the top dark web market.
- Most dark markets have user review systems and vendor ratings to establish trust.
Hence, it should be the top priority to track these platforms and shut them down as quickly as possible. If you take a quick look through darknet marketplaces, you’ll instantly notice an overwhelming supply of pirated content. We’re talking about even early access to unreleased music, leaked TV episodes, concert footage, and even popular video games before they officially drop. But somewhere between production and purchasing, things can get dirty. For example, an insider or factory employee might quietly slip away with an unmarked gun and sell it online. Once it lands on a darknet marketplace, it becomes part of the illegal weapons trade.
Payment Methods Overview
You can use dark web monitoring tools, such as NordVPN’s Dark Web Monitor, to check if your data has been leaked. These tools scan dark web forums and marketplaces for any signs of your compromised credentials. There is no need to visit darknet marketplaces yourself to know whether your data was leaked.

Rise And Fall Of Silk Road
The marketplace is well-known for its bug bounty programs and robust security mechanisms, including mandatory 2FA. Cybersecurity companies and researchers monitoring darknet markets face legal and ethical restrictions. Legally, they are limited to observing publicly accessible areas using tools like the Tor browser, without engaging in unauthorized access or illegal transactions. Immediately change your passwords, enable two-factor authentication, and notify your bank or credit card provider if the leaked information includes your financial data. You should also consider freezing your credit to prevent identity theft. On one hand, it offers privacy for whistleblowers, journalists, and citizens in oppressive countries.
When he’s not empowering PrivacySavvy’s readers to take control of their online security, Saheed enjoys distance running, playing chess, and exploring the latest open-source software advancements. If you think the Dark web marketplaces are just online shops, you’re wrong — these sites are the actual weapon stores for criminals. They provide criminals with access to everything they need, from launching attacks to stealing data, etc. They sell these files for just a fraction of the original cost on the surface web or even share freely, which makes them tempting for people looking for shortcuts. While it might be tempting, remember that downloading such content has serious legal and cybersecurity risks. One of the things STYX is infamous for is having a rigorous verification process for users that makes it seem more exclusive.
In 2025, darknet marketplaces primarily accept Monero (XMR) and Bitcoin (BTC). Privacy-focused operators are shifting to Monero due to its default anonymity, compared to Bitcoin’s transparent ledger Darknet markets see BTC inflow drop to $2B. Darknet marketplaces remain central to illicit trade in 2025, with evolving business models, payment systems, and law enforcement responses.

Unmasking The Dark Web Economy: Key Hubs And Cybersecurity Implications

For those who are looking for a reliable Alphabay Market alternative, Awazon Market aspires to become the solution. Now, that is not to say illegal behavior is completely beyond detection. The dark web combines encryption, anonymity, and hidden doorways to provide the perfect sanctuary for such illicit activity compared to the usual internet, which is more vulnerable and trackable.

Those who use these services can still be traced and prosecuted if caught, especially as law enforcement continues to sharpen its tracking tools. Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content. The markets often share materials related to child exploitation, pornography, and non-consensual recordings, all of which are serious crimes that inflict lasting harm on real-life victims. Such content fuels a dangerous cycle of abuse, violence, and exploitation. Plus, there’s a thorough vetting process for new buyers and sellers to keep the community more secure.
The fallout for victims whose data is stolen and sold can be devastating. They suffer losses such as identity theft, financial loss, and emotional distress due to damage to their personal and professional lives. They really don’t care about the loss and dilemma of the victims whose data has been stolen.



