Governments also often set up “honeypot” sites on the dark web, which mimic illegal services and wait for users to enter their info. Of course, this sort of site poses no risk to legitimate dark web users, but it’s worth knowing that your usage of the dark web in general might draw attention to you. If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web. You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. You can now safely browse dark web websites and hidden wikis, but if you plan to do anything more than that, you’ll need to take several precautions.
While Tor offers anonymity by routing your traffic through a decentralized network of nodes (onion routing), it shouldn’t be your only line of defense for privacy. Malicious actors and government agencies can run Tor nodes, compromising privacy and security. In fact, there have been instances where attackers controlled hundreds of Tor nodes. The Deep Web includes unindexed content like private databases and password-protected sites accessible with standard browsers. Many people use it for privacy-focused communication, whistleblowing, or accessing restricted information in censorship-heavy regions. Platforms like SecureDrop even allow journalists to receive tips anonymously.
Tips For Staying Safe On The Dark Web
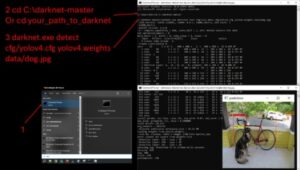
Instead, you need to get the Tor browser to access the dark web. Make sure that when you download the Tor file, it’s from their official website. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users.
Are Dark Web Search Engines Illegal?
If you now open whatismyipaddress.com in another browser, such as Edge, you will see that you are using a different IP address in the Tor browser. If the Tor browser is running, you can immediately check whether it is working as intended. To do this, go to the website whatismyipaddress.com, for example. A look with the Tor browser at a darknet directory such as the uncensored Hidden Wiki reveals that seemingly anything goes on the darknet.
- This infects a user’s device and essentially blocks them out of it until they pay a “ransom,” usually in the form of cryptocurrency (so it’s harder to track and recover).
- Some hackers offer ransomware as a service (RaaS), where cybercriminals can “rent” a strain of ransomware from its creator in exchange for a fee or a percentage of their ransom payments.
- As much as the dark web is supposed to promote free speech alongside bypassing censorship, many shady activities occur there.
- You risk being targeted for attacks if you explore the dark web without protection.
How To Browse The Dark Web Legally
Staying safe and anonymous often means continuously educating yourself, adapting your methods, and refining your tools. Ultimately, the Dark Web is neither purely nefarious nor inherently virtuous—it’s a dynamic environment shaped by the motivations and actions of its users. Your decisions, responsible conduct, and awareness of potential risks will determine your experience in this hidden realm. As the most widely used anonymity network, Tor routes your internet traffic through a series of volunteer-run servers (relays) around the world. This “onion” routing masks your IP address and encrypts your data multiple times, peeling away layers of encryption at each relay.
Encrypted Communication Tools
- Never install extensions or additional add-ons, even if they seem useful.
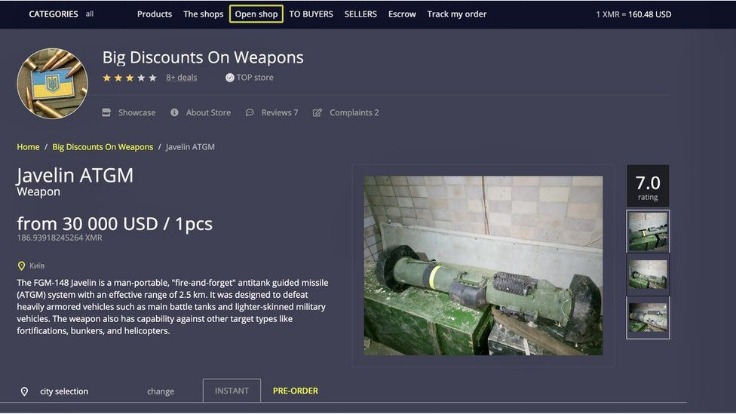
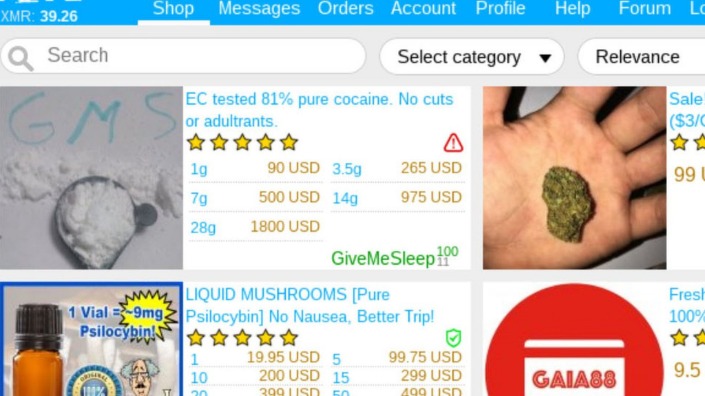
- The market facilitates trades in stolen credit card data, hacked bank accounts, and services to facilitate the laundering of cryptocurrency.
- Learn how darknet markets function and the challenges they present to cybersecurity, shedding light on the hidden side of the internet.
- Like other marketplaces, it also requires registration for new users and accepts payments in Monero.
- This means you have to know someone who is already using the platform.
- This is a great way to improve your privacy because Tor isolates each website you visit, meaning third-party trackers and ISPs can’t reveal your identity.
It is based on Chromium, the open-source of Google chrome but the developers claim to have removed all Google tracking software and that the browser stops other companies from tracing you too. Unlike the open web, these sites aren’t really worried about being found by on-page SEO tools like web crawlers. While there are Google-like equivalents trying to categorize the dark web, results are spotty. There are some supposed ‘dark web’ search engines like Torch or Haystak is said to have indexed more .onion sites than any other search engine. While it is not flawless in protecting user privacy, it works well enough to give users much more privacy in where they go, the content accessed, and protecting their identity and location.
Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. Therefore, the legality of the dark web will mainly depend on how you use it. You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom. The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity.
Cybersecurity Best Practices For Protecting Your Digital Assets
Being cautious while browsing the dark web is essential, as significant risks are involved. This can lead to incrimination for other activities later in life. China, for example, uses the “Great Firewall” to restrict access to popular sites and prevent citizens from evading government restrictions. Indeed, Facebook, The New York Times and now even the CIA have sites on the dark web, hosting “onion” versions of their pages that can be accessed via the Tor browser. The spy agency is hoping to securely and anonymously collect tips, though its entire website, including job listings, are available on the onion service. Learn how darknet markets function and the challenges they present to cybersecurity, shedding light on the hidden side of the internet.
Darknet Websites Uncovered
For example, legitimate sites, such as the BBC, the New York Times, ProPublica, and Facebook, have made their sites accessible as a Tor Onion URL to help people avoid government censorship. As well as phishing scams, a multitude of other scams operate across the dark web. There are many fake marketplaces and platforms that might offer to sell you goods or services but actually take your money without providing anything in return. Since the dark web is unregulated, there’s almost nothing scam victims can do to seek justice or compensation.
How Can I Increase Security While Using Tor?
The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing. For this reason, you cannot browse through these sites using your default search engine. Using the ProtonMail .onion site offers security and privacy advantages. Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection. This makes it even harder for third parties to see your email traffic. The social media giant is also aware of the many attempts by repressive regimes to restrict its access.
You can look for information on /r/deepweb, /r/TOR, or /r/onions, of which the latter is useful to find hidden wikis and more. Many of these Reddits have rules prohibiting linking to illegal sites and services, so you likely won’t find anything illegal there. Put simply, the deep web is all the information stored online that isn’t indexed by search engines.
Users need a special browser with added software to access the tor dark web in the first place. There are also millions of servers which only store data which can’t be accessed via a public web page. Data brokers such as LocalBlox for instance crawl the web and store information about business and consumers to sell for marketing purposes. Browsers such as Google, Bing, DuckDuckGo act like virtual librarians, sorting and cataloging materials so they can be easily searched.
Tails is a mere 1.3 GB download, so on most connections it will download quickly. You can install it on any USB stick that has at least 8 GB of space. Tails works on most computers manufactured in the last 10 years. You can either sell or buy goods on the dark web, but both present difficulties. In opennet mode, the network will automatically assign you to other users on Freenet’s network.