
I’ve worked with family-owned businesses that nearly went under after getting hit with a wave of fraudulent purchases. The data then gets parsed, sorted by bank type and location, and sold in batches. One compromised payment processor or e-commerce platform can yield thousands of card numbers at once. They’ve essentially created a parallel economy with its own reputation systems, escrow services, and even customer support channels. Rather than individual hackers working alone, the reality is that we’re dealing with sophisticated criminal enterprises that function like businesses, complete with customer service and quality guarantees.
What Should I Do If My Card Is Stolen?
Louis DeNicola is freelance personal finance and credit writer who works with Fortune 500 financial services firms, FinTech startups, and non-profits to teach people about money and credit. His clients include BlueVine, Discover, LendingTree, Money Management International, U.S News and Wirecutter. You also have the right to add a fraud alert to your credit reports. When there’s a fraud alert on your report, creditors can see that you might be the victim of identity theft and are instructed to verify your identity or contact you before extending credit in your name. ⁴ Child members on the family plan will only have access to online account monitoring and social security number monitoring features.
Heating Up Productivity: Top 5 Features Of Fireberry Revealed
Credit card fraud on the dark web operates quite differently from what many people imagine. To avoid entering your personal information into a spoofed website, it’s important to learn how to spot a site that’s been spoofed. When a card is skimmed, the threat actor obtains all its information including the cardholder name, number, expiration date and Card Verification Code (CVC). Flare monitors the clear and dark web as well as illicit Telegram channels for high-risk external threats to your organization. All content provided on Web Design Booth is for informational purposes only and does not constitute professional advice.
Web Hosting Company Increases Security Team Bandwidth With Up To 80% Decrease In Threat Research Times
- Monitoring the activity on these platforms is crucial for fraud detection, brand protection, and financial intelligence.
- It provides them with valuable information needed to carry out a variety of attacks.
- This free service includes a credit report card analysis and monthly score updates and monitoring.
- Quality and validity of the data it provides justify its higher cost over other marketplaces.
- Since it was established in 2020, Real and Rare has been considered to be a stable credit card site that suffered very few downtimes.
This is the Songstress Style Holowear for Gardevoir which is obtained by through a spceial event Treasure Chest. This Holowear is a new rarity of Holowear which includes animations for Moves, movement, Unite Moves and more. He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests. Whilst a great many products are sold, drugs dominate the numbers of listings, with the drugs including cannabis, MDMA, modafinil,108109110 LSD, cocaine, and designer drugs. Prior to joining CSO, John wrote and edited articles for PortSwigger’s The Daily Swig covering topics including web security, vulnerabilities and hacking culture. For more than 17 years, John covered a wide variety of topics including network security and enterprise technology for The Register.
The Age Of Infostealers Is Here Is Your Financial Service Secure?
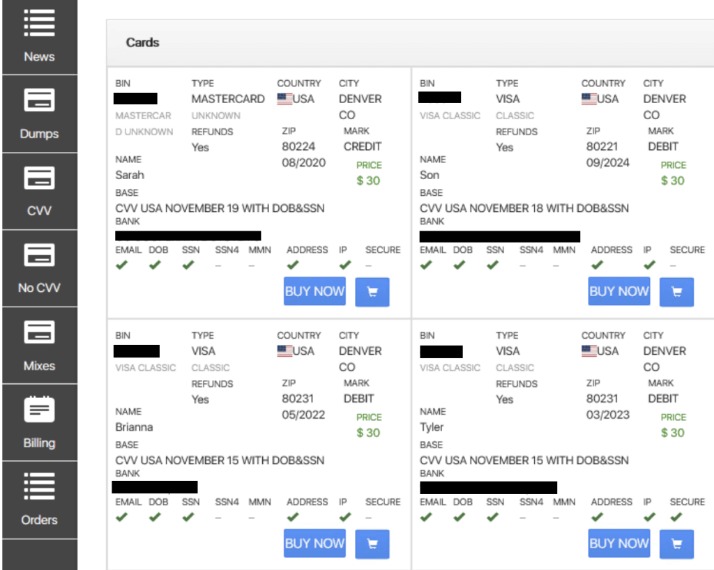
He said some fraudsters would go as far as setting up entire businesses using merchandise bought with stolen credit card information, like a guy who flipped refrigerators, beds, and mattresses. These stats highlight the scale of credit card fraud on dark web markets. 1 Next, we’ll look at how this sensitive data ends up for sale online. The dark web makes it easy to buy and sell stolen cards anonymously.
How Do I Check My Credit Score?
We strive for accuracy and authority, but it is recommended to consult with qualified professionals before making decisions based on our content. Web Design Booth may receive compensation from third-party advertisers, which does not influence our editorial content. Knowledge and vigilance are key defenses against this growing problem. The threat actor behind the AllWorld Cards marketplace has a clear goal in mind. They are actively promoting the platform on Dark Web hacking-related platforms since late May 2021.
Best For In-depth Tools: CreditWise From Capital One

Also, learn about the common tricks scammers are using to help you stay one step ahead of them. If you see unauthorized charges or believe your account was compromised contact us right away to report fraud. With Chase for Business you’ll receive guidance from a team of business professionals who specialize in helping improve cash flow, providing credit solutions, and managing payroll. Choose from business checking, business credit cards, merchant services or visit our business resource center.
Some of the offers on this page may not be available through our website. If your phone number is exposed on the Dark Web, a scammer could contact the provider and convince them to transfer your number to a new SIM — in the scammer’s possession. You can set a SIM code in your security settings to stop this type of attack and protect against hackers trying to access your data and linked accounts on your smartphone. Two-factor authentication (2FA) is an additional layer of cybersecurity that prevents someone from accessing your online accounts even if they have your password or username. With 2FA enabled, your email, online banking, and other accounts will require a secondary authentication method to access — such as a one-time-use code or biometrics (such as your fingerprint or facial scan).
These platforms serve as hubs for cybercriminals to buy and sell compromised payment card details. Deep and dark web credit card sites are illicit by definition since they focus on selling various illegal products that enable threat actors to carry out financial fraud, money laundering, and other crimes relating to credit cards. Stolen credit cards and their details are added and bought on these shops on an hourly basis, and more and more markets launch a matching forum and/or a Telegram channel to keep expanding and supporting criminal online activity. The adult-oriented social networking service The FriendFinder Network had 20 years’ worth of user data across six databases stolen by cyber-thieves in October 2016. What’s more, the vast majority of the exposed passwords were hashed via the notoriously weak algorithm SHA-1, with an estimated 99% of them cracked by the time LeakedSource.com published its analysis of the data set on November 14, 2016.
In The Pok�mon Of The Week Department

It’s important to note that the dark web is legal to use, but is known for illegal dealings such as stealing people’s personal and financial information. And with almost £2 billion lost to cybercrimes last year according to Action Fraud, people are being asked to stay vigilant to protect their money. If you receive an alert, it means we’ve found your personal information on the dark web. You can’t remove the info once it’s there, but you can take action to protect it and help limit fraud. Eliminate unmanaged credentials, reduce password risk, and manage access across legacy, unfederated, and shadow IT apps with 1Password Device Trust.
That means it has observed some fascinating cosmic wonder every day of the year, including on your birthday. After that, Premium costs $24.99 per month and Family costs $34.99 per month for one adult. Get unlimited access from EUR 0.003 per request + a subscription fee. Fill out the form or reach out to us at email protected to get access. Fields may contain null values which suggests that cards may be one or the other. And beware—while many explore out of curiosity or for research purposes, it’s important to remember that engaging with these platforms, even as an observer, can lead to serious legal and ethical consequences.
Equifax spent an estimated $337 million on improving its technology and data security, legal and computer forensic fees and other direct costs alone. Dubsmash acknowledged the breach and sale of information had occurred and provided advice around password changing. However, it failed to state how the attackers got in or confirm how many users were affected. The “meticulously gathered and maintained” database offered comprehensive behavioral, economic, and social profiles of the vast majority of the Chinese population. Researchers believe that one collection, named “tw_db” contains Taiwan-related details.

Cybercriminals moved laterally through their ingress points before stealing credentials that allowed them to query its databases, systematically siphoning off stolen data. US authorities charged four named members of the Chinese military with masterminding the hack. Attackers broke into Equifax’s systems between May and July 2017 by taking advantage of an unpatched Apache Struts vulnerability to hack into the credit reference agency’s dispute resolution portal. Patches for the exploited vulnerability had been available since March 2017, months before the attack. Struts is a popular framework for creating Java-based web applications. Bob Dyachenko, cybersecurity researcher and owner at SecurityDiscovery.com, and cybersecurity website Cybernews stumbled on the billions of exposed records during a research project.
To buy Bitcoin with a credit or debit card, choose the bank card payment option. For transactions of $150 or more, you may need to complete a brief KYC process for added security. Offer pros and cons are determined by our editorial team, based on independent research. The banks, lenders, and credit card companies are not responsible for any content posted on this site and do not endorse or guarantee any reviews.



