That said, the Tor Browser and a VPN make an excellent team for protecting your online activities from prying eyes, and provide optimal online privacy protection. Go to the directory where you downloaded the Tor Browser installation file. Right-click on the downloaded file and select “Extract Here.” Once the Tor Browser setup files have been extracted, double-click on “Tor Browser Setup” to install the browser.

However, the default settings aren’t the farthest you can go. Users can take further steps to maximize privacy when browsing with Tor. Likewise, you’ll experience slower browsing speeds when browsing via Tor, as your requests get bounced through several servers before being processed. You can download the Tor browser from the official website, Torproject.org. The browser is available on Windows, macOS, Linux, and Android.
Tor Browser For IOS
Identifying specific individuals who use the dark web can be quite tricky. However, we advise connecting to one of our recommended VPN services to stay anonymous. There are a few reasons why the dark web isn’t stopped or shut down.
- This can often be for political reasons, but also because they may be involved in illegal activities, such as the ones listed above.
- The developer, Akshay Bhasme, indicated that the app’s privacy practices may include handling of data as described below.
- Antivirus is a great way to stay protected while using the Tor browser or the dark web.
- Like standard browsers, Tor has an address bar where you’ll type the domain you want to visit.
- Hence, it’s advisable not to download files via Tor, especially from unknown sources.
- Similar to onion websites, I2P lets you access hidden I2P websites (also known as eepsites).
Table Of Contents
Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers. There’s no broad consensus on dark web safety, but you at least need to use Tor and VPN together. Once you have those, there are several ways to tunnel through the dark web. It makes up about 6% of the internet, and it’s where you find everything from illegal marketplaces to forums for whistleblowers. The Tor Browser provides 3 levels of security — Basic, Safer, and Safest.
- The dark web is a small section of the deep web that is hidden on purpose, requiring specific software to access.
- While Tor provides a high degree of anonymity by routing your internet traffic through multiple servers, thereby masking your IP address, it isn’t infallible.
- But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network.
- It’s designed as an environment to elude detection, where site owners and visitors hide their identities.
- Access the dark web securely and privately with our redesigned Tor-based browser for iOS.
Browse Privately
Dark web forums are online platforms that can only be accessed using anonymous networks, mainly Tor…. In many countries, the installation and use of Tor are perfectly legal. However, using the Tor browser for illegal acts is possible since the network has increased anonymity. Aside from the potential for illegal actions, certain countries, such as China, Iran, and Russia, have banned it completely. You are spoilt for choice with an extensive server network of over 7,600 in more than 118 countries. These servers support P2P activities no matter where you are.

If your information has been compromised, then it’s likely that your phone number is also on the dark web. For a number of technical reasons, it’s much faster and more reliable than Tor. The peer-to-peer routing structure is more advanced, and it does not rely on a trusted directory to get route information. I2P uses one-way tunnels, so an eavesdropper can only capture outbound or inbound traffic, not both. Due to all the nodes that your traffic passes through, Tor by itself significantly limits bandwidth. Adding a VPN to it, even a fast one like IPVanish will make it even slower, so please be patient.
Wide Area Network (WAN): Definition, Examples, And Technologies
Tor for Android is developed by the Tor Project itself, while the Onion Browser is the recommended option for iOS users. These browsers offer the best security and privacy for browsing the dark web on mobile devices. There are many excellent VPNs for the dark web, but my favorite is ExpressVPN because it’s the fastest on the dark web. I also like NordVPN and ProtonVPN, as they offer dedicated Tor servers that allow you to access .onion sites directly from regular browsers like Chrome. I’ve put together detailed guides on how to access the dark web safely on both Android and iOS. I also share essential tips for staying secure there — personally, I always use a VPN for added privacy since Tor isn’t completely secure on its own.
Words Of Caution When Using Dark Web Sites
If so, it’s better to use the onion address instead of the standard one. You can access many other sites via the Tor browser, and your requests will be routed through multiple servers to avoid monitoring. However, some websites consider Tor traffic suspicious and make users jump through several hoops, including CAPTCHAs. Others outrightly block Tor users from accessing their platform, so you might not be able to open some popular platforms. If you want to access the dark web, your first step toward a more private experience should be to secure your internet connection and data with a reliable VPN.
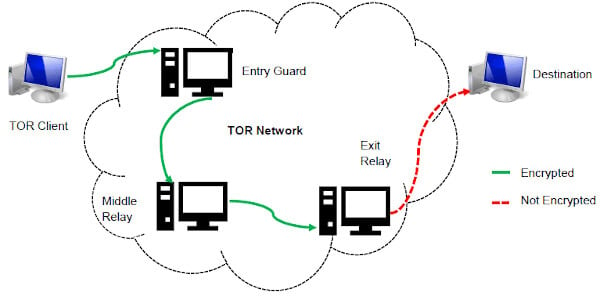
I2P’s most attractive angle is to access its own internal eepsites, which are its version of .onion sites. It is definitely a strong contender for the best, strongest, layered encrypted web browser. It is free, open-source, and based on a hardened version of Firefox. For most people, it will be the best and safest starting point. It is the closest thing to a full dark web online anonymity suite. The browser routes your traffic through a global network of volunteer-run servers (sometimes called nodes), encrypting your data and masking your IP address multiple times.
Learn To Use Tor On An IPhone To Browse Anonymously
Unlike regular browsers that directly connect to websites via your ISP’s DNS, Tor anonymizes your journey by routing your request through several relays before reaching its destination. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web.

Are Sites On The Dark Web Illegal To Use And Visit?
The Basic level enables all features and scripts, making it the most susceptible to attacks, such as script injection. The Safer level enhances security by disabling certain features, and the Safest level entirely blocks scripts, which may impact some functionality. Once connected, you should be redirected to the browser’s homepage. Check out some of the top legal Dark Web sites to get started. Go to the Google Play Store and download the official Tor browser.
How To Install The Tor On Android
Its layout engine displays online pages effectively on Android devices such as smartphones or tablets, delivering an optimized browsing experience. Whonix uses Oracle Virtualbox to run two virtual machines (VMs) on top of your currently installed OS (Windows, Linux, or Intel-based macOS). The Whonix Gateway VM handles Tor processes, and the Whonix Workstation VM runs user applications on an isolated network.
Enhancing Your Security
When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. The core principle of the Tor network was first developed by U.S. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online.



