
Designed for cybersecurity teams, Lunar enables advanced threat detection, credential leakage monitoring, actor profiling, and tactical intelligence extraction—at scale and in real time. Uncover the threats that are relevant to you by leveraging Lunar’s continuous monitoring of the deep and dark web. Talk to one of our cyber experts to learn how Lunar equips your team to uncover hidden threats and gain visibility into conversations that matter most. Additionally, the ability to create large, private groups and dark web telegram channels significantly compounds the challenge for cybersecurity teams. Within these closed ecosystems and forbidden Telegram channels, threat actors can coordinate and operate with little risk of detection.

How Do I Access The Dark Web?

The project is widely regarded as a cornerstone of internet anonymity, supporting activists, journalists, and individuals in restrictive regions worldwide. The Dark Web isn’t a place for everyone but it’s worth exploring some parts of it. For those who may be a little faint of heart – we have listed 50 Legit Dark Web sites you can visit. By following these precautions, you can explore the dark web with a greater degree of safety and security.
It is a private search engine that lets you search the regular internet via Tor. This allows you not only to visit sites with the added privacy provided by the Tor network, but also search the web as privately as possible from inside the Tor browser. In addition, it is worth noting that users should not blindly trust links on the Hidden Wiki because this is a community resource that anybody can update, and some of the links are malicious.
The Dark Lair – Comprehensive But User-Friendly Directory
Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. Some users also share links on encrypted apps like Telegram or Keybase that you can check. To help you avoid these issues, my team and I tested dozens of .onion sites and found the best ones that provide uncensored access to information while keeping you anonymous online.
ZeroBin — The Secure Way To Share Your Pastes
- In a world where digital privacy feels as rare as a unicorn, the dark web offers a peculiar sanctuary.
- The email service is available both on the surface and on the dark web.
- Articles are published regularly and include interesting information, images, and quotes from officials.
- For this reason, it is always better to use a trustworthy VPN for Tor while accessing the Dark Web, as this will provide a robust additional layer of privacy.
- You can also search for onion links on DuckDuckGo’s onion page by clicking Onionize.
- Founded around 1999 by activists in Seattle, it has since grown to over six million users worldwide.
Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. It works by sending internet traffic through volunteer-operated nodes all over the world.
Installing The Tor Browser
Our mission is to offer reliable tech help and credible, practical, science-based life advice to help you live better. As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web. For obvious reasons—I don’t want to get you or me into trouble, after all—I’m not going to get too specific when it comes to what you can find for sale on the dark web. A lot of transactions are handled via cryptocurrencies such as Bitcoin, which is relatively (but not completely) private and anonymous.
The famous social media platform has a prominent presence on the dark web. However, we do not advise readers to log onto this dark web mirror site; doing so would risk their privacy and that of others. But we are on the dark web, you can’t trust anyone, so there may be sites containing illicit content. You must review the site’s descriptions before you click to open them. When you try to enter a .onion website, it will reroute your access request around the internet, bouncing it off three random servers before you reach the target website.
- The release of Freenet in 2000 is considered by many as the start or founding of the dark web.
- Below are the main categories of dark web sites in 2025, along with examples of what users typically find in each.
- This includes sites with publicly accessible content, such as news portals, blogs, and social media platforms.
- This double encryption also protects against compromised Tor entry nodes that could potentially monitor your activity.
Other Privacy Tools And Services
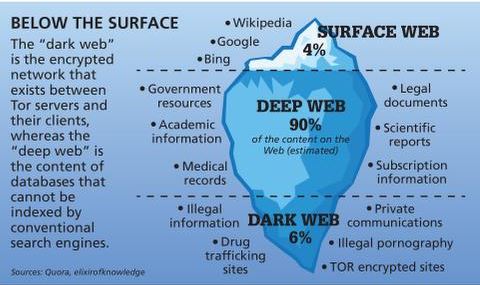
It includes media and archives which cannot be crawled and indexed with current search engine technology. In a world where digital privacy feels as rare as a unicorn, the dark web offers a peculiar sanctuary. Yet, it’s not all cloak and dagger; the dark web is a complex realm with legitimate uses and potential pitfalls. The best onion links in 2024 serve as portals to this hidden layer of the internet, where anonymity is both a shield and a double-edged sword.
We are reader supported and sometimes earn a commission if you buy through a link on our site. The Dark Web and Darknets offer valuable spaces if you value privacy, freedom of speech, or research security technologies.If you misuse them, the consequences can be severe. Unlike the Deep Web, Darknets are intentionally hidden and designed to preserve privacy and anonymity. There are estimated to be 1.1 billion websites on the Surface Web as of 2025 (Internet Live Stats). Cyble plays a key role in this landscape, offering AI-powered threat intelligence and digital risk protection. By consistently following these verification practices, you can greatly reduce risks and confidently navigate the dark web, ensuring your security and peace of mind.
Radar Rundown Private search engines use the metasearch or proxy search model and the proprietary cr… The dark web is a part of the deep web that contains websites not included in the mainstream search engine index. Accessing the dark web is legal in itself; the nature of the activities you engage in ensures it stays that way. Criminals prefer the dark web because it offers anonymity like never before. But as long as you don’t knowingly engage in illicit activity on the dark web, you are completely fine. The developers of ProtonMail recommend using the Tor browser to visit the dark web version of the service.

Google Feud
Therefore, it makes for a useful multi-purpose search engine – no matter what you’re looking for. SecureDrop is software platform that NGOs and media organizations can install to accept leaked information from whistleblowers safely. It also comes with a functionality that allows journalists to communicate with their source(s) in a private manner. Many news sites use SecureDrop, such as The Washington Post, ProPublica, and The Guardian. It was created by the U.S Navy with the purpose of helping informants in foreign nations to communicate safely over the Internet.
To contribute a tip, join the community, which can be done anonymously through an approved onion link. The site is strongly resistant to hackers and encrypts your data in transit as well as the rest. Among many open-source whistleblower sites, SecureDrop is currently a leading platform. Many prominent media sources and journalists maintain a presence on this website location to securely accept documents from anonymous senders. These include big names, such as Al Jazeera, CBC, Forbes, Huffington Post, The New York Times, and many more. When you’re dealing with sensitive information, nothing feels truly anonymous or private.
It encrypts your connection, ensuring anonymity as you explore the dark web. It’s also important to note that your activities on the dark web aren’t completely immune to web tracking, and the expectation of anonymity can create a false sense of security. You can run a dark web scan to see if any of your data has leaked onto the black market. And if you think you’ve fallen victim to identity theft or fraud, be sure to report the internet scam just like you would any other crime. Yes, you can access the dark web on a smartphone, but you’ll need an appropriate browser, like Tor browser for Android or Onion browser for iPhone. Remember that phones can get viruses just as easily as computers, and the chances of getting a virus likely increase when you’re browsing dark web mobile sites, no matter your platform.
Watch for unexpected changes in system performance that could indicate malware. Cryptocurrency miners and other malicious software often target dark web users. Using a reliable antivirus to scan your device is worthwhile if you spot suspicious spikes in system resource usage. KeyBase combines encrypted messaging with secure file sharing and identity verification.
What Kind Of Information Can I Find On Dark Web Search Engines?
The keyword in that example is “onioname,” which is right at the start of the .onion link. With a readable site name like that, people will know what to expect when they click on the link. The website has received six Pulitzer Prizes for its grassroots-based journalism. Accessing it through an onion link is much more convenient if you’re unable to directly view it on your screen. Switzerland-based Proton (formerly ProtonMail) is one of the most secure email services, and has a reputation for not logging IP addresses. If you care about your privacy on the Internet, no other site comes close.



