These are just like regular websites but use the special .onion domain name. Another problem is that Tor makes the IP addresses of all public Tor exit nodes public(new window), making them very easy for governments to block. The dark web is just misinterpreted; it is not intrinsically dangerous.
What Is The Dark Web And How Do You Access It?
- However, if no one accesses data for a long time, it can disappear (this works much like BitTorrent, where files that aren’t actively seeded become de-indexed over time).
- If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough.
- Cybercriminals often disguise malware within legitimate-looking files to trick users into compromising their own security.
- When used in unison, these tools seal the security and privacy vulnerabilities of the Tor network, keeping you anonymous as you roam the streets of the dark web.
- Once you’ve established a Tor connection, you can connect to onion dark websites.
However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail. For more information, read more about the most secure email service providers in my other post. Now that you’ve completed the download, it’s time to install the Tor browser on your device. (The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously.
Law enforcement agencies in many countries monitor the dark web to combat illegal activities. Cracking down on many illegal marketplaces on the dark web is the result of such monitoring. So, you risk being flagged or investigated for visiting certain sites, even without criminal intent. On the other hand, the deep web is the hidden part of the Internet that contains private or restricted content that is not indexed by search engines.
Also, try its services risk-free with the 30-day money-back guarantee. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. This is high-level protection; no one can intercept your data or activities.

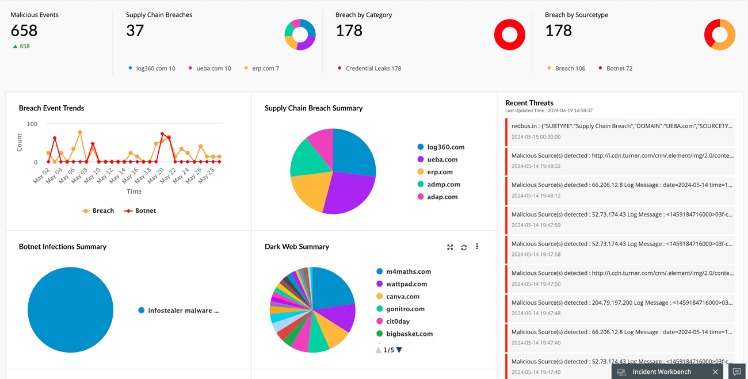
Used ethically, such as for privacy or study, one can search this area lawfully and safely. Combined with smart surfing behaviour and technologies like Tor and a VPN, even the darkest reaches of the internet may be securely traversed. Look for features like real-time alerting, coverage of multiple dark web forums and marketplaces, credential and data leak detection, and integration with your existing security stack. Strong vendor support, customizable alerts, and compliance alignment are also key to ensuring the tool delivers actionable insights, rather than just noise. The history of the Dark Web reflects the intricate interplay between technology, privacy concerns, and the ever-evolving landscape of online activities. Malware, ransomware, and hacking tools are also readily available for purchase or rent, enabling attackers to launch sophisticated campaigns.
The spouses of Ashley Madison users received blackmail letters demanding they pay $2500 in Bitcoin or have the infidelity exposed. Infamous examples of Dark Web sites include the Silk Road and its offspring, such as Dream Market. The Silk Road was a website for the buying and selling of recreational drugs, and a lot more scary things besides. This is akin to the things you actively hide from other people and don’t want anyone else to learn about.
Tor-Enabled OS Alternatives To Tails For Secure Dark Web Browsing
If you want to improve your security further, you could also use a VPN at the same time as Tor. For the most security-conscious, you can even install the Tails operating system on a flash drive and run Tor from that. Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff. If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node.
Accessing On Windows And Mac:

If you’re lucky enough, you can find it on clearnet privacy forums. In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites. This is where an Onion website, like the Tor browser, comes in handy. If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. Perhaps the best-known thing you can buy on the Dark Web is information collected in what seems like the almost daily data breaches we read about in the news. That information can include checking and credit card account numbers, social security numbers, and other sensitive information.
Advantages Of VPN Over Tor
For similar reasons, the dark web is more resistant to surveillance. Whistleblowers, journalists, and other professionals at risk of targeted surveillance use the dark web to communicate sensitive information. For example, whistleblower Edward Snowden used TAILS(new window) to help stay one step ahead of the NSA. Because of their closed nature, these darknets also make it impossible to know how many people actually use Freenet. However, on top of this basic file-hosting framework, volunteers have developed applications that allow for websites, message boards, and more.
- Illegal cyber activity cannot necessarily be stumbled upon easily but tends to be much more extreme and threatening if you do seek it out.
- If you see inaccuracies in our content, please report the mistake via this form.
- The open web, also called the surface web, includes any public web content that is indexed by search engines.
- To help find functioning .onion URLs, look to dark web directories and forums — Reddit users recommend tor.taxi, tor.watch, daunt.link, or one of the Hidden Wikis.
- The content produced on this website is for educational purposes only and does not constitute investment advice or recommendation.
- Users should exercise caution and follow safety practices to minimize risks.
Safety First: Browsing Tips

Once connected to Tor, you’re ready to begin exploring the dark web. However, keep in mind that the dark web is not organized like the regular internet. Instead of search engines, you’ll need to rely on directories or specific .onion links. For an additional layer of security, consider using a Virtual Private Network (VPN).
It’s Not A Wrap-up For You!
The U.S. Federal Bureau of Investigation (FBI) arrested Ulbricht in October 2013, but imitators still arise, many much larger. No one can force you to visit a drug-selling site, give out your info, and buy cocaine or something else. As long as you pick your sites carefully and use a safe and secure VPN, you’ll remain untouched and be able to browse this internet space indefinitely.
The dark web represents a concealed layer of the internet that is inaccessible through conventional search engines. While it accounts for a relatively small portion of online activity, its significance is disproportionate to its size. Studies estimate that only 0.01% of websites globally are accessible via the dark web, yet these platforms host a disproportionate volume of illicit activities. By definition, the dark web is the home to the darker corners of the internet. These corners are deliberately concealed from the public eye and require specialized tools and browsers to access, making it more difficult for the average person to explore.
Tips For Safe Access To The Dark Web
Quality and validity of the data it provides justify its higher cost over other marketplaces. The platform’s popularity continues to grow, attracting both new and returning customers. Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem. To expand their reach, some marketplaces established parallel channels on Telegram.
By exploring these categories of resources, users can discover that the dark web’s landscape is more nuanced than popular portrayals suggest. Education, activism, journalism, and creativity all find refuge here, protected by layers of anonymity. However, it’s vital to approach each new platform with caution—vetting its authenticity, reputation, and purpose before fully engaging.



