
Some marketplace operators first build trust by running a legitimate platform. Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content. The markets often share materials related to child exploitation, pornography, and non-consensual recordings, all of which are serious crimes that inflict lasting harm on real-life victims. Such content fuels a dangerous cycle of abuse, violence, and exploitation. While hiring a hacker might sound like something out of a movie, it’s a very real threat. Businesses may use these services to sabotage their competitors, while individuals may seek revenge or simply want access to private information about someone.
Abacus’s Rise To The Top Of The Western DNM Ecosystem
CoinJoins of all sorts, stealth address solutions like silent payments and BIP47, and encouraging users to run their own node and use non-custodial and open-source software where they can. Now that you have a decent idea on why such markets are so important, I’ll do my best to explain why bitcoin is not used there anymore. Bitcoin’s adoption depended on markets like Silk Road to pioneer, and what was special about Silk Road is that it was an almost completely free (as in freedom) market. Free markets are excellent for adoption because they don’t require bureaucracy, permits, regulations or any other form of permission to run.
Discover everything about what a darknet market is, top marketplaces, security threats on them, and learn how to protect your data online. The horizontal bars represent each market lifetime, i.e., the time when the market becomes active until its closure, and is colored according to the market’s monthly trading volume in USD. In the vertical axis, markets are in the chronological order of their launch date, although for some markets the activity effectively starts after the launch date (e.g., AlphaBay). The largest component of the S2S network one year before and one year after the operation Bayonet. Nodes are sellers that are active within the time period, and an edge is placed between two sellers if at least one transaction occurs between them during the period.
Network Structure Of Transactions
Chainalysis data shows darknet marketplace revenue dropped post-Hydra seizure in 2022 but recovered to $2 billion in Bitcoin inflows during 2024 Darknet market BTC inflow drop and shift to Monero. Abacus alone represented nearly 5 per cent of total DNM revenue, underscoring the ongoing scale of underground commerce. Its extra layer of encryption has afforded protection to activists in oppressive regimes fighting for civil rights and free speech. SecureDrop has been used by journalists to communicate with anonymous sources, and encrypted email service ProtonMail developed by MIT and CERN is another well-known denizen of the darknet. The CIA has its own ‘onion site’ on the Tor network, encouraging foreign intelligence sources to share secrets without fear of detection or reprisal. Chainalysis data shows that about 0.14% of all transactions in crypto, some $50 billion, involve illicit activity, with a rise in stablecoins as an illicit payment mechanism.
CoinDesk 20 Performance Update: Chainlink (LINK) Declines 43% As Index Trades Lower
- Investigators noted that the operators likely shut everything down and left with user funds.
- One thing that distinguishes BidenCash on the dark web, however, is how it markets itself.
- First, while the dataset is preprocessed with state-of-the-art methods, there is no ground truth for validation, and this uncertainty propagates to our findings.
- Their pseudonymous nature enables criminals to exploit blockchain technology for financial crimes, challenging regulators and law enforcement.
- Sites such as Abacus and Russian Market accept both currencies to broaden their appeal.
Opinions expressed herein are those of the authors and not necessarily those of Analytics Insight, or any of its affiliates, officers or directors. As digital finance evolves, striking a balance between innovation and security is crucial. Implementing AI-powered fraud detection, enhancing oversight, and promoting responsible adoption will help build a more transparent and resilient crypto ecosystem. Whereas, Pyramid schemes focus on recruitment rather than legitimate products, often disguised as crypto investments.
Trading, buying or selling cryptocurrencies should be considered a high-risk investment and every reader is advised to do their own research before making any decisions. Abacus’s exit follows the June 16, 2025 law enforcement seizure of Archetyp Market, marking the latest in a series of shutdowns in the Western DNM ecosystem. Sometimes, you might be hacked by using weak passwords or even just connecting to unsecured Wi-Fi on public networks.

Background research tasks included learning from past drug lords, researching legal matters, studying law enforcement agency tactics and obtaining legal representation. Patterns recommended to avoid include hiring hitmen like Dread Pirate Roberts, and sharing handles for software questions on sites like Stack Exchange. Moreover, the number of multibuyers increases, which suggests a fast response from buyers to external shocks by trying to diversify their sources. Tracking funders helps researchers understand the global distribution of research funding. For example, researchers may be interested in knowing which countries provide the most funding for research in their field or how funding patterns have changed over time 52.
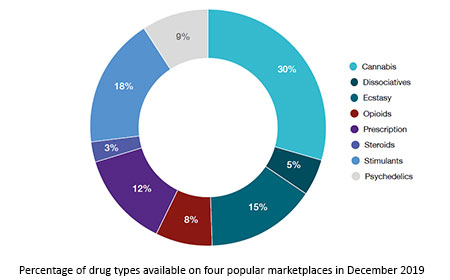
What Exactly Is Sold On These Marketplaces?
- However, the dark web is so complex and vast that if law enforcement takes down one market, it pops up elsewhere.
- Following the removal of Monero from mainstream exchanges, darknet marketplaces had little choice but to revert to Bitcoin for transactions.
- “After major exchanges delisted XMR, we observed a significant increase in bitcoin inflows,” Jardine said in an interview with CoinDesk.
- These different regimes suggest that the ecosystem’s resilience is mainly supported by the high demand of buyers rather than the response of the sellers.
- In this example, we’re going to run through the steps for purchasing CBD oil off the darknet, but the same procedure can be used to acquire any one of the several thousand items listed on popular DNMs.
- The paper calculates the number of users based on IP addresses and country codes and presents the number of users in anonymous networks on the Darkweb.
Later in 2022, the US Naval Research Laboratory built on Freenet’s idea to create a secure and encrypted network for sensitive communications, which was later released to the public as open-source software. And, of course, think twice before sharing too much personal details online. That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web.
Improved Security Protocols
As it stands, DarkMarket and White House Market appear to be the largest darknet markets in the Western world with over 300,000 customer accounts each. White House Market saw a 40% increase in users between August 27 and September 28, following the exit scam of Icarus, and a further 8-10% increase between late September and October 20. Governments must adapt rapidly, crafting agile legal frameworks that balance innovation with accountability. Private cybersecurity firms must strengthen partnerships with regulators to track illegal transactions and monitor emerging threats.
Budget, Financial Reporting, Planning And Performance
Those who use these services can still be traced and prosecuted if caught, especially as law enforcement continues to sharpen its tracking tools. The fallout for victims whose data is stolen and sold can be devastating. They suffer losses such as identity theft, financial loss, and emotional distress due to damage to their personal and professional lives. They really don’t care about the loss and dilemma of the victims whose data has been stolen.
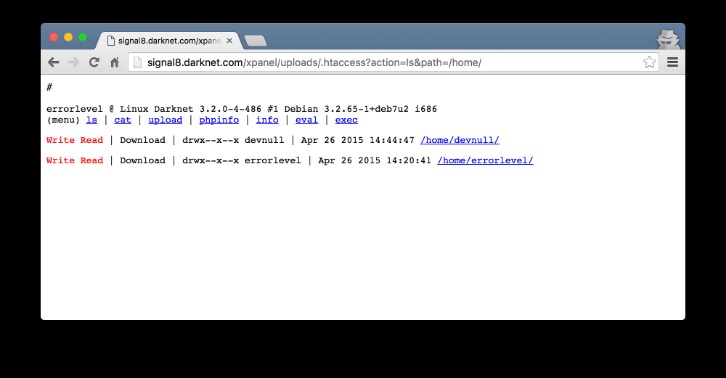
While some of these markets were shuttered by law enforcement agencies – some took the easy way out with exit scams. Here are some of the now-defunct dark web markets that were notorious for cybercrime. Some dark web marketplaces even host content that’s not just illegal but extremely harmful, so it’s really important to understand the risks before diving in.
GoldMelody’s Hidden Chords: Initial Access Broker In-Memory IIS Modules Revealed
When you access the pedestrian Internet, you are directly communicating with websites. But when you’re accessing a website through TOR it’s like asking another user to ask another user to ask another user to fetch the webpage information for you. Shop for exclusive products in our marketplace, where privacy, security, and anonymity are always a top priority. This being said, the most private methods would then be Bitcoin (properly CoinJoined) or monero privacy and even payments in other altcoins. The leaked FBI briefing is just one of hundreds of thousands of files from Blueleaks, a cache of police documents illegally exfiltrated by hacktivist group Anonymous.
HUDSON INTELLIGENCE, LLC
Nevertheless, due to their unregulated nature, DWMs exhibit behaviours not observed in regulated marketplaces. They offer anonymity to their users by using and developing specialized tools. DWMs are accessed through darknet browsers supporting the onion routing protocol (e.g., Tor), which provides anonymous communication connections35. Additionally, transactions are made with cryptocurrencies, mostly Bitcoin, which also provide anonymity to the transaction parties6,36. While the Bitcoin blockchain is publicly available on Bitcoin core37 or other third-party APIs such as Blockchain.com38, a market or a user can generate a new address for each transaction.



