It routes users’ traffic through thousands of volunteer-run servers called nodes/relays. These nodes/relays and the websites operating on them make up the Tor network, or as it is more generally named, the dark web. JavaScript is a programming language used by websites to add interactive features, such as videos, forms, and dynamic content. However, on the dark web, JavaScript can also be exploited by hackers to track your activity or deliver malware to your device. To reduce the risk of these threats, it’s highly recommended to disable JavaScript when browsing dark web sites. That doesn’t mean it’s impossible to track users on the dark web.
Components Of DOT Security’s Services
All you have to do is replace “.onion” at the end of the onion URL with “.onion.to”, “.onion.city”, “.onion.cab”, or “.onion.direct” and you should be good to go. Tor stands for “The Onion Router,” and the Tor Browser is essentially a modified version of Mozilla Firefox with integrated scripts and other add-ons to protect your privacy. The browser is preconfigured to connect to the Tor Network and mostly works independently. Gannicus Oliver is an experienced tech journalist (he loves writing on emerging techs and digital privacy issues) and an online business consultant. In his free time, Gannicus enjoys uncovering thrilling adventures and traveling around the world.
Neither ZDNET nor the author are compensated for these independent reviews. Indeed, we follow strict guidelines that ensure our editorial content is never influenced by advertisers. Well, as long as you don’t visit sites with underaged models or that engage in human tracking or that sell drugs and other illegal items. One of the major advantages of using Tor in overly-restrictive countries is that it keeps your online travels private. Unfortunately, some oppressive regimes have figured out a way to block Tor traffic.
More On How To Stay Safe On The Dark Web
Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe. However, there are plenty of legal and legitimate online activities that require privacy and anonymity.

Private Internet Access
Treat every site as untrusted unless you’ve verified it from multiple sources. This hides your Tor usage from local networks, masks direct Tor connections, protects against network-level surveillance, and reduces the risk of being flagged for accessing privacy tools. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access. These can include the previously mentioned illegal offerings, but can also include ultra-private information designed to be shared only with certain parties. The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web. In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe.
- This means you can use your favorite browser instead of the Tor Browser and still benefit from being routed through the Onion Network.
- The Tor Onion Browser is essential for accessing the dark web, designed for user anonymity.
- To access the dark web safely, it’s necessary to use a dark web browser like Tor in combination with trusted dark web directories and search engines to help you find reliable sites.
- During testing, we connected via the US free server and fired up the Tor browser.
Downloads

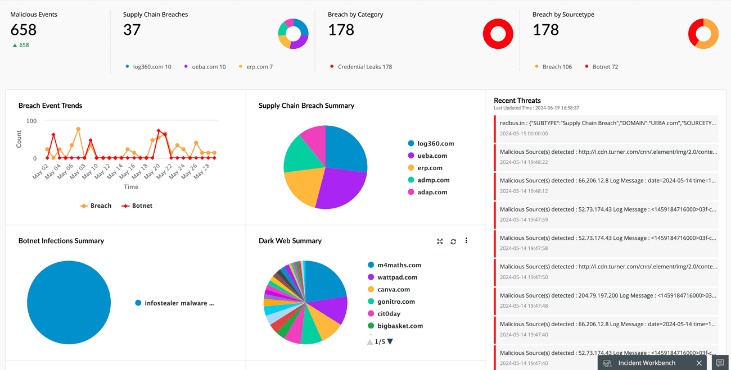
The dark web limits online tracking, and there are many legitimate reasons people like journalists and activists use the dark web to remain private. But there are also many illegal activities that happen on the dark web. And just like in real life, using the dark web for criminal purposes is never legal. The Tor Project says that of the 2 million people using Tor every day, only 1.5% of them are accessing hidden or dark websites (that’s 30,000 people). Most dark web websites are in English; according to one estimate, a staggering 78% of information on the dark web is in English.

How To Access Dark Web?
The dark web offers both benefits and risks for users going into it, but the intent of the user will also impact this. The dark web contains a wide variety of services and content, some of which skirts or disregards legality. Though the intention and purpose of users on the dark web may vary, the dark web itself is neither good nor bad.
Step 3: Securely Connecting To The Network
- A top-of-the-line VPN network that ensures maximum security while accessing dark sites online.
- Conversely, the Darknet mode allows you to create restricted anonymity networks of people you only trust or know to share content with.
- We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch.
- The features make NordVPN viable for accessing the dark web as your IP address can’t find out that you are using Tor.
- I advise sticking to well-known, reliable sites and taking extra precautions to ensure your security.
While this isn’t an issue for most of the trip (since each relay only has access to the previous and next relays in the network), it is an issue with the exit node. Because of the relaying of data through the onion nodes, and the encrypting and decrypting taking place at each node, your internet connection will slow considerably. This means the Tor Browser is not recommended for streaming video, playing games, or downloading large files. This encryption and relaying of your browsing data prevents anyone who is watching from detecting which websites you are visiting.
After completing the operations and completing the bridge connection, click the “Connect” button in the same window. The terms “dark web” and “deep web” are sometimes used interchangeably, but they actually refer to different aspects of the internet. The dark web has also been used for other nefarious activities, such as the sharing of child pornography and the planning of terrorist attacks.
We can conclude that this portion of the internet can be dangerous but again, you’re in control and decide which websites you want to visit. However, the line is drawn at what you’re doing once you’re on the dark web. Engaging in illegal activities—like buying drugs, trafficking stolen data, or distributing harmful content—is absolutely against the law. In the U.S., dark web usage has been growing steadily—not just among cybercriminals, but also among privacy-conscious users. Once downloaded, you can establish a connection to the Dark Web.
However, they won’t work on Chrome, regular Firefox, Safari, or some other browser that you might use. Tor can also run off a USB flash drive, is portable, and comes with a preconfigured browser to protect your anonymity. The US military initially developed Tor which later on became open source and publicly funded. The Tor browser is available for use on Windows, Mac, OSX, or Linux without the need for installing any software.
Google’s purpose is to show the most relevant information to all of its users quickly and easily. That means that Google wants to minimize the amount of time users spend searching for certain queries. Did you know that Google only shows you a glimpse of all the websites that actually exist? The last time I checked, it’s estimated that the entire web is roughly 500 times larger than what Google returns in Google Search.



