To use the dark web safely, use as many privacy-enhancing tools or programs as you can, and do not identify yourself in any way to anyone for any reason. While visiting any of the sites you find on those Wiki sites, do not maximize your browser, as it can help identify you by your monitor resolution. Tor Browser is available in multiple languages in a single multi-locale download, which can be changed using the menu in General settings. Get Avast BreachGuard for Mac to protect your privacy and keep your personal data from falling into the wrong hands. Get Avast BreachGuard for PC to protect your privacy and keep your personal data from falling into the wrong hands.
Why Use Tor For Accessing The Dark Web?

The middle node knows the previous node but not your IP address or what you’ve requested online. The exit node knows what you’ve requested and connects you to it, but it doesn’t know your device and its IP address. The dark web contains much of the internet’s illicit content, ranging from drug trafficking to child pornography sites. Alternatively, users can connect in opennet mode, which automatically assigns peers on the network. Unlike darknet mode, opennet uses a handful of centralized servers in addition to the decentralized peer-to-peer network.
I2P cannot be used to access .onion sites because it is a completely separate network from Tor. Instead, I2P uses its own brand of hidden sites called “eepsites”. Even when using security measures and your common sense, accessing deep web content still poses a risk.
Tor-over-VPN Vs VPN-over-Tor: The Right Order
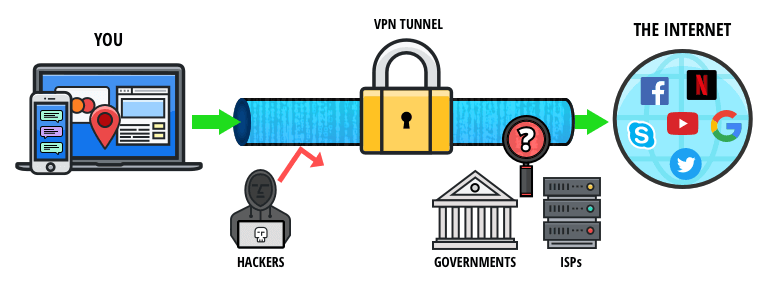
Tor Browser masks your IP address and routes traffic through multiple servers. It’s extremely rare and only useful in very specific cases, like if your VPN is only accessible through Tor. With this setup, your ISP sees Tor usage, and your VPN provider sees the final traffic after it leaves Tor. Setting up Tor correctly is critical if you want to browse the dark web without exposing your real identity.
How To Get On The Dark Web Using Tor Browser
It assigns a task to the client instead of the server, eliminating server-related vulnerability. ZeroBin is a wonderful way to share the content you get from dark web resources. It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee. SecureDrop is a dark web link that allows whistleblowers on the dark web to communicate and share information with journalists safely and without being tracked. It allows you to search for images, maps, files, videos, social media posts, and more.
Quick Comparison: Best Anonymous Dark Net Browsers
Therefore, you need to use the Tor browser, which, by far, is not only the safest Onion browser but also is easy to use. As a rule of thumb on the dark web, you should never use a default browser to search for anything on the deep web. Install Avast SecureLine VPN for iOS to protect your privacy and keep your data from falling into the wrong hands.
Tor-Enabled OS Alternatives To Tails For Secure Dark Web Browsing
When using Tor, practice good security hygiene by avoiding suspicious links and using reliable antivirus software. It’s simply a part of the internet designed to offer anonymity and privacy. While it does host illegal activities and shady content, it also supports legitimate uses like secure communication for activists, journalists, and whistleblowers in oppressive regimes. The dark web itself is neutral; how people use it is what makes it good or bad.
The biggest and most frustrating part about dark websites is that they live for a short span of time. These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. Using the ProtonMail .onion site offers security and privacy advantages. Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection. This makes it even harder for third parties to see your email traffic. It is the dark web’s version of Wikipedia with a massive links directory.

People often make the grave mistake of divulging their private information to the seller or anyone else who can take advantage of it and harm the user in many ways. This, joined by incredible value and the price of around $2/mo, makes PIA very attractive. Unfortunately, it’s slower than NordVPN and ExpressVPN but overall, its performance is admirable in practice.
- Use aliases and avoid any activity that might reveal your identity.
- The internet is almost unfathomably large, and most of us are only actively engaging with between 4-5% of it.
- Sections of the dark web are often closed down too, as part of police operations.
- Each node knows only part of the journey, making it extremely difficult to trace your real location.
- This typically involves entering the proxy type, address, and port, and potentially authentication details if required by the proxy server.
- However, it\’s important to note that Tor doesn\’t automatically discover Dark Web websites for you.
Tips For Staying Safe On The Dark Web

However, it is often prohibited for ISPs to sell your data to third parties. During that period, on top of the risk of accidental disclosure and theft, governments and the police could ask ISPs to share data. With all this data, your ISP could create a very accurate profile of you and link it to your IP address.
Separate Your Real Life From Your Online Persona
- By definition, the dark web is the home to the darker corners of the internet.
- If you engage in illegal activities or access illegal content that could implicate you in a criminal offense, you may face serious legal consequences, including fines and imprisonment.
- People who live under a government that deeply supervises or censors internet traffic eventually get attracted to the dark web.
- You’ll appreciate its added features, such as Threat Protection, which shields you from malware and trackers.
- Even if they aren’t actively malicious, they might still have weak security or expose you to threats.
But if you want to claw back some of your data from the brokers and miners, downloading and using Tor is a free and easy way to do it. Because Tor traffic is routed through multiple servers, it is often slightly slower than normal web traffic. It would be problematic if someone could open your private email chains through a simple Google search. An easy way to think about this is if you need a username and password to access it, it’s a part of the deep web. If someone’s caught buying or selling illegal items like credit card numbers or hacked data, they can face serious federal charges—even if it all happened behind an anonymous screen. From real-time alerts vetted by Cyble’s Security Operations Center (SOC) to AI-driven risk tagging, Cyble enables faster, more informed response decisions.
The dark web limits online tracking, and there are many legitimate reasons people like journalists and activists use the dark web to remain private. But there are also many illegal activities that happen on the dark web. And just like in real life, using the dark web for criminal purposes is never legal.
Dark Web Search: The Best Dark Web Search Engines In 2025
All you’ll need is an 8GB thumb drive, an installation package, and a couple of minutes to get things up and running. By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web. For recommendations on choosing a VPN, look for expert reviews and articles.



