Services like Random Chat connects you with random people using the same service. If you’ve ever checked your medical results online through a portal that required a login, you were navigating the deep web. It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. 80% of top markets now use escrow networks, up from 60% in 2023. Drughub excels in pharmaceutical dark pool trading with 15,000+ listings and $2M monthly via BTC. Serving 8,000+ users and 600+ vendors, it holds a 10% share of drug commerce—an emerging force since 2023.
Scams And Fraudulent Activities On The Darknet Markets
I say this as someone that lost a tiny amount of coins on the Evo exit scam and a slightly larger sum during the Silk Road raid. Encrypt your address with the vendors key and save it to your clipboard. So import the vendors key, type out your name and address in full, including country if the source is from abroad.
How To Access The Dark Web On An IPhone
Encrypted communication channels on the dark web allow users to message back and forth in an anonymous online environment. However, some surface web platforms like ProtonMail offer encrypted email services in addition to dark web versions that enable people residing in more repressive areas to communicate freely. There are thousands of websites on the dark web, many—but not all—of which are illicit marketplaces selling stolen personal data. Learn more about the kinds of sites that can be found on the dark web and how you can access them. Then, try LifeLock free for 30 days to help find out if your personal data is leaked on the dark web. The dark web marketplaces thrive on the demand for illegal services and extreme content.
Dark Web Tools & Services
Medical records, fee-based content, membership websites, and confidential corporate web pages are just a few examples of what makes up the deep web. Estimates place the size of the deep web at between 96% and 99% of the internet. Only a tiny portion of the internet is accessible through a standard web browser—generally known as the “clear web”. Unlike Tor, I2P is designed for peer-to-peer services like file sharing, email, forums, and even decentralized websites — all within its own closed network. Its distributed nature makes it more resistant to central points of failure.
Is It Illegal To Use The Tor Browser?
- Its 12,000+ users and 900+ vendors rely on a 95% trust rating, making it a go-to for quality-focused trading in the onion network.
- Not just Tor alone, there are official sites for downloading every similar web browser APK.
- To access darknets, users typically need to download and configure the Tor Browser; a modified version of Mozilla Firefox that routes all traffic through the Tor network.
- Only two VPN providers that we know of, AirVPN and BolehVPN, offer this service, although neither of these score highly for speeds.
- If your device is unprotected, you could be a victim of malware or a hacking attack.
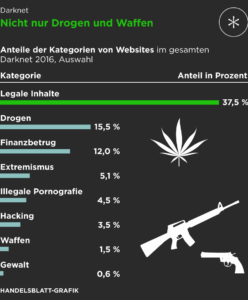
- Carding refers to the theft and illegal use of credit card information, and the dark web offers a platform for criminals to sell and buy such information.
I personally don’t use tails, but it’s pretty highly recommended to use it if you can, it provides a whole lot of security. These days, it can seem increasingly difficult to protect valuable assets and data from the reaches of threat actors. This is particularly true for enterprise organizations working with sensitive data in key sectors like healthcare, energy, and finance. That’s why it’s more critical than ever to go on the offensive. This is where things might get just a bit confusing, as the Dark Web is nearly synonymous with illegal activity.

VPN Alternatives For Securing Remote Network Access
The dark web is used by journalists, whistleblowers, and political activists who need the protections that it offers. Anything you need to do that has to be off the books to some extent, for noble or ignoble reasons, can be done on the dark web. The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment). Part of what makes the dark web the dark web is that you can’t access it through your normal web browser, nor can you look something up on it via a Google search. The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight.

Anonymity Through Tor

VPNs are also used for accessing geo-locked content hosted by streaming services. The best VPN options are paid-for and subscription-based, as many free options will either throttle your speed or collect your data. First — and this is strongly recommended — you should install a Virtual Private Network (VPN). Also, you need to use a privacy-focused browser such as the Tor network to connect via nodes and proxy servers, which are more secure and aim to anonymize traffic requests. The Tor browser is able to access the special domain names, with the suffix .onion, used in the dark web.
The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. The same anonymity that publishers enjoy on the dark web can be utilized by users who want to read the available information. Again, people who live in countries where the freedom of the internet is limited, for example in China, can really benefit from using Tor. Later on, the underlying Tor code was released into the wild under a free license, leading to the formation of the Tor Project. In 2008, the first Tor Browser was released, making it easier for any internet users to access the dark web.
However, the markets are dominated by things like illegal drugs, explicit content, pirated files, hacking services, and stolen personal information, among others. This is another book that focuses on the privacy that the dark web offers instead of the illegal activities happening there. As the name of the book indicates, it is a beginner’s guide for staying anonymous on the internet. But it can be useful for even experienced dark web users who want greater insights. In today’s climate, where data breaches and invasive surveillance have become commonplace, understanding how to access the Dark Web and its underlying technologies is becoming increasingly relevant.
Internet Archive Audio
Dark net websites are called “Tor hidden services”, and they can be distinguished from normal websites by their URLs. Instead, download Tor, the most secure and user-friendly option for accessing .onion sites. Despite some skepticism about its origins and privacy due to its military development, Tor remains the preferred choice for safe dark web navigation. Darknets are not limited to criminal activities; nation-state actors use these hidden platforms for espionage, disseminating propaganda, and recruiting agents.
There are several whistleblower sites, including a dark web version of Wikileaks. Pirate Bay, a BitTorrent site that law enforcement officials have repeatedly shut down, is alive and well there. We don’t want to leave you with the impression that everything on the dark web is nefarious or illegal. The Tor network began as an anonymous communications channel, and it still serves a valuable purpose in helping people communicate in environments that are hostile to free speech.
Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine. To access the dark web, you’ll need a specific set of tools – more about that later in the step-by-step section. Lokinet is easier to set up than I2P, and it may run faster than Tor in some cases, especially when visiting regular websites through its secure network. However, its network is still small, and there aren’t many hidden services available yet.
- Best of all, Digging the Deep Web is written in plain, easy-to-understand English, and you can read it in one sitting.
- Fraudulent activities on the dark web include phishing scams, fake identity sales, and the sale of fake products.
- Since each node server in the Tor network is volunteer-operated, you never know who operates the relays that your data is traveling through.
- If you’re after secure email, look for the Proton Mail service.
The Tor network was created by the US military in the 1990s for anonymous communication between spies over the internet. That effort was never fully realized, but the US military published the code under a free license in 2004. Researchers from the Electronic Frontier Foundation and other groups continued its development and launched the Tor project in 2006 as a tool for journalists, activists, and whistleblowers. For built-in Tor over VPN functionality, NordVPN operates specialized servers that automatically route you through the Tor network.

Many people use it for privacy-focused communication, whistleblowing, or accessing restricted information in censorship-heavy regions. Platforms like SecureDrop even allow journalists to receive tips anonymously. If you engage in illegal activities or access illegal content that could implicate you in a criminal offense, you may face serious legal consequences, including fines and imprisonment. Accessing the Dark Web, a part of the web that isn’t indexed by standard search engines, is not illegal in most countries. People use it for various legitimate reasons, such as bypassing censorship in restrictive countries. The dark web hosts various types of illegal content, such as stolen data, child exploitation material, and prohibited items.