
Cracked is one of the few dark web forums operating openly on the surface web. It focuses on hacking tutorials, vulnerabilities, and combo lists, organized into 12 language-specific subforums. RAMP supports multilingual communication but heavily favors Russian users.
How To Stay Safe On The Dark Web
The interface works smoothly, but it usually loads slower due to Tor routing. Adamant offers blockchain-based secure messaging without needing phone numbers or email addresses. The platform stood out during my testing for its commitment to anonymity — all messages are fully encrypted and stored on a decentralized network. It’s particularly useful for sensitive communications that need to remain private. The dark web is neither entirely a haven for illicit activities nor a utopian space of limitless freedom. Instead, it represents a complex ecosystem where anonymity can serve both noble causes—such as protecting free speech and enabling investigative journalism—and darker ends.
Absence Of Malicious Content And Practices

Fortunately, you can’t just stumble onto dark web websites by accident. Info like your name or email address never needs to be shared on the dark web. You should also limit the number of financial transactions you make on Tor banking portals.
- By closely monitoring market movements, we offer in – depth analysis that empowers businesses and individuals to make strategic decisions.
- They will definitely have to arrange regular meetings where they can brainstorm and discuss each other’s ideas and how those ideas can be implemented globally.
- ZeroBin encrypts and decrypts text in the browser, so their servers have no way of knowing what’s happening on the browser side.
- It supports operations in multiple languages and operates on both clearnet and Tor.
- Forums play a crucial role in shaping the dark web’s social landscape, enabling users to exchange knowledge, share security advice, and discuss market reputations.
Cybersecurity Blogs And Forums

It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web.
Rise Of Malware-as-a-Service (MaaS)
It has operated since 2008 and remains resilient despite its founder’s 2018 arrest. Notably, LeakBase bans data leaks involving Russian entities, indicating a politically calculated stance seen in many dark web forums. Archive.today stores snapshots of web pages for later access, much like The Wayback Machine.
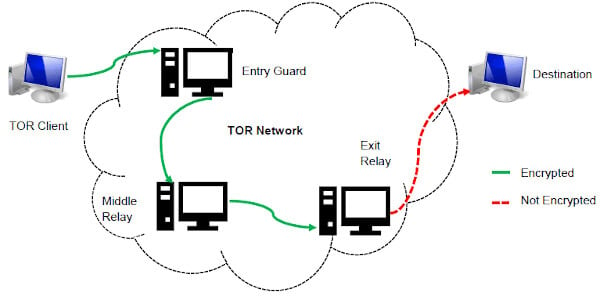
For most people and use cases, using only a VPN will offer sufficient privacy with much faster speeds than Tor alone. A VPN provides strong security for everyday browsing without the extra delays, middle checkpoint, and then finally the exit gate. The extra connection layers can act as a significant burden to your browsing experience if you’re doing something that is bandwidth intensive. This sequence offers less anonymity because your real IP address is still partially exposed along the Tor path. Plus, it’s slower since your data travels through the same four steps – entry node, relay node, exit node, and then the VPN server.
Onionname – Personalize O URL Do Seu Site onion
It was quite popular in the previous year and the trends show that it would be more popular in the current year. STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity. In 2025, the dark web presents an evolving array of threats, significantly impacting businesses and individuals alike.
Whereas the deep web is the part of the web not searchable by traditional search engines and requires special tools to access it. Also, you must log in or have a specific IP address or URL to access the deep web content. The biggest and most frustrating part about dark websites is that they live for a short span of time.

Why Do People Want To Regulate The Cryptocurrencies The Dark Net?
They will definitely have to arrange regular meetings where they can brainstorm and discuss each other’s ideas and how those ideas can be implemented globally. Instead of banning them, there should be regulatory frameworks developed that can help regulate the use of cryptocurrencies; otherwise, it can be disastrous for the economy. Creating a new organization under the banner of the United Nations to regulate and monitor the use of cryptocurrencies. On the dark web, links could be a step in the right direction to address this issue. The creation of a new organization under the banner of the United Nations to regulate and monitor the use of cryptocurrencies. On dark web links is a potential solution to address the challenges posed by the illicit use of cryptocurrencies.
- This is especially valuable for people in censorship-heavy regions or under surveillance.
- Better yet, create an alias specifically for browsing and never reuse it elsewhere.
- Not all onion sites are dangerous, but many host illegal, harmful, or deceptive content.
- It’s been around for many years and helps users navigate the dark web by curating links to various resources.
- Now that you understand the essentials of anonymous networks and how to prepare yourself for secure browsing, it’s time to explore the practical steps involved in accessing the Dark Web.
- During my testing, I found its categorized index particularly helpful for discovering trustworthy sites across various topics.
If you find a link that is not working let us know on our contact page. mark it means it has been verified as a scam service and it should be avoided. With the above dangers, it’s imperative to tread carefully as you step into the dark web. Users are advised to exercise caution and conduct thorough research before engaging in transactions. The site also provides valuable resources for developers and those interested in contributing to the project. However, given the nature of some products on the Dark Web, users are advised to exercise caution.|At the heart of our mission is a commitment to providing users with verified, up-to-date, and safe onion directories to help navigate the dark web responsibly. The Hidden Wiki and its alternatives offer valuable gateways to deep web content that isn’t accessible through conventional search engines. However, the dark web environment can be unpredictable and sometimes dangerous, filled with scam links, phishing sites, and other malicious threats.|ZeroBin offers an extra secure version of this service by only encrypting and decrypting text in the browser, meaning their servers have no knowledge of what is passing through it. Based in Switzerland, ProtonMail is an encrypted email service that is very popular with cryptocurrency enthusiasts. Facebook is aware of attempts by many governments to restrict access to a tool that allows strangers across the web to talk and collaborate freely.|Your activities on the dark web are not entirely shielded from tracking, and relying solely on anonymity can lead to a false sense of security. The dark web draws not only serious cyber criminals but also law enforcement agents aiming to catch them. Feather is a free and open source Monero wallet available on most major computer platforms.}

Deep Search
Haystak offers an uncensored yet privacy-focused search engine experience. It indexes a large number of .onion links and offers a premium version that includes tools to filter searches, track search history anonymously, and browse with stronger protections. Haystak does not censor content by default but provides safety flags to help users make informed decisions. Dark web search engines are specialized tools that allow users to perform web searches within the dark and deep web. Unlike traditional search engines like Google or Bing, these tools operate on the Tor network — a hidden ecosystem where most content is intentionally obscured from public view. Instead of browsing indexed links, dark web engines scour encrypted, often anonymous websites (“.onion” sites) that do not exist on the clear or surface web.
The Legality Of Accessing The Dark Web
Today, buyers and vendors look for reliable alternatives that offer security, escrow protection, and a strong vendor community. The number of malicious tools, or “drainers,” designed to steal cryptocurrency assets like tokens and NFTs saw a substantial rise. Unique threads discussing drainers on dark web forums increased from 55 in 2022 to 129 in 2024, with Telegram channels serving as prominent hubs for these activities. The BBC Tor Mirror is a testament to the fact that there are some very good websites on the darknet as well. The BBC site on the dark net is the official dark net version of the British media house.
Cryptocurrency exchanges can play a big role in the regulation of cryptocurrencies. Our data is available to the public free of charge, and we encourage you to use it to inform your personal or business decisions. If you choose to republish our data on your own website, we simply ask that you provide a proper citation or link back to the respective page on Market.us Scoop. We appreciate your support and look forward to continuing to provide valuable insights for our audience. The Tor network provides powerful tools for enhancing online privacy and anonymity, but these benefits come with certain trade-offs.



