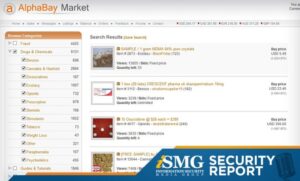
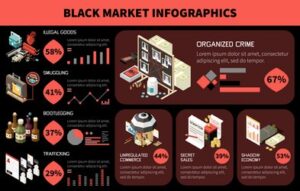
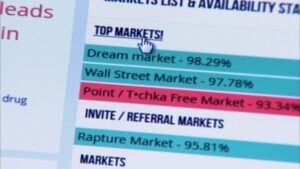
Typically, any reference to the visible web will be to common websites with a familiar internet domain extension. Google considers the majority of the content on the entire web highly irrelevant and useless to its users. That’s why such a large percentage (as much as 94%) of the entire web is not returned in Google Search. Also, we’d like to point out that several dark net sites face technical issues and remain inoperative temporarily or shut down permanently.
A premium user has access to the private Telegram channels that include an exclusive leak channel that’s unavailable to regular members. It is a forum on the darknet that’s designed like X (formerly Twitter). Like a lot of other forums in a similar domain, Pitch is significantly focused on corporate access, hacking, and data leaks, making it a communication hub where hackers and cybercriminals gather. Discover the top thirteen dark web forums where cybercriminals gather and cybersecurity researchers spot emerging threats. This part of the internet is notorious for illegal activities, facilitated by the anonymity it offers.
To understand the dark web discussion groups needs more than looking at the data that’s leaked. It required maximum attention by looking at who leaked what, where it was posted, and in what type of context. A quick guide for developers to automate mergers and acquisitions reports with Python and AI.
Exposure To Malware And Scams
It is a specific Debian-based version of Linux software that leaves no traces of the user activity or the operating system on the computer. It uses the Tor network because it is a popular network that helps to circumvent censorship and online surveillance. The Torrez market is one of the biggest dark net marketplaces, also called a community-driven marketplace. It contains a good selection of product listings that range over 35,000 items.
Report It To The Authorities (if It’s Safe To Do So)
It was a dominant forum that featured a dangerous threat for average users within the Russian-speaking cyber environment. It had a surface web mirror alongside an onion site that users accessed using the Tor browser. As per our research, the forum served as a place where hackers had discussions revolving around malware, unauthorized access, sales, database trading, and security vulnerabilities.
Boost Your Privacy When Browsing The Web With A VPN

However, they also play an important role in how these groups orchestrate and monetize their attacks. These sites provide the ransomware operators with a platform to accept payments from the victims, a space to shame them and apply pressure, and somewhere to leak their data if they don’t pay. As I’ve mentioned, the dark web isn’t just a place of eternal torment, teeming with drug dealers, human traffickers, and a hitman.
Don’t Stick Your Nose Where It Doesn’t Belong
There are also many tools that can be use to monitor the dark web and scan for personally identifiable information and even respond to attacks. First, in the USA, it is a federal offense to use the USPS for any of these transactions. If the buyer or seller gets caught, there are significant legal ramifications. DNMs have a limited life and may be shutdown suddenly, leaving users with unfulfilled orders and sellers with no means of communication. BidenCash and other exit-scam markets such as Torzon and Kingdom Market collapsed between 2022 and 2024. They used “free data dumps” and emotional marketing to build trust before vanishing—an enduring lesson in the risks of social engineering.
Tor And The Darknet
I2P can only be used to access hidden sites that are only available on the I2P network. Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN. Rule No.41 allows a federal judge to issue a search and seize warrant for any person who is using anonymity software like Tor. But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web.
Tor Browser: Accessing The Darknet
When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. The dark web is a very popular platform for journalists, political bloggers and political news publishers, and in particular, those living in countries where censorship shields most of the internet. In 2002 the dark web began to grow significantly when researchers backed by the U.S. The Tor Network provided a way to open safe communication channels for political dissidents, while also offering a channel for American intelligence operatives to communicate from around the globe.
- Use cryptocurrency to buy anything, and use a disposable email address for any type of communication on the dark web.
- One notable fact is that the site has changed its domain twice since its formation.
- It aims to expose abuses of power and betrayal of public trust through investigative journalism.
- Even after Silk Road went down, dark web marketplaces haven’t slowed down.
Onion sites are websites on the dark web that use the ‘.onion’ top-level domain. They can only be accessed through the Tor browser, which encrypts your connection and masks your IP address, providing anonymity. However, any illegal activities conducted on the dark web, such as purchasing illicit goods or engaging in criminal behavior, are still punishable by law. Discover how to explore darknet market links safely while ensuring your privacy and security. See how our intelligent, autonomous cybersecurity platform harnesses the power of data and AI to protect your organization now and into the future. Darknets also serve as a platform for whistleblowers and privacy advocates.
While pressed pills are often made with vitamins, it’s impossible to know that the additives are safe. Note that loading sites with TOR usually takes considerably longer than on the clearnet. It may take anywhere from 15 seconds to several minutes for a page to load, depending on network and site demand. This highly popular English-language market sold all varieties of narcotics. Many of these markets operate internationally, and some have certain specialties.


Law enforcement agencies monitor many dangerous markets, and even anonymous browsing isn’t foolproof. Just visiting these sites can attract attention from law enforcement, especially if you interact with known vendors or download suspicious content. Dark web markets work much like regular e-commerce websites but with extra layers of anonymity and encryption. Buyers browse listings, place orders, and pay with cryptocurrency — typically Bitcoin or Monero — to obscure transaction trails.
(Presentation and polish isn’t quite so important on this part of the internet.) Click on any website link, and it’ll appear on screen, with its address at the top. Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn’t know exactly what you’re doing. Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS. Try LifeLock free for 30 days to receive notifications if we find your personal information on the dark web and help protect against identity theft.
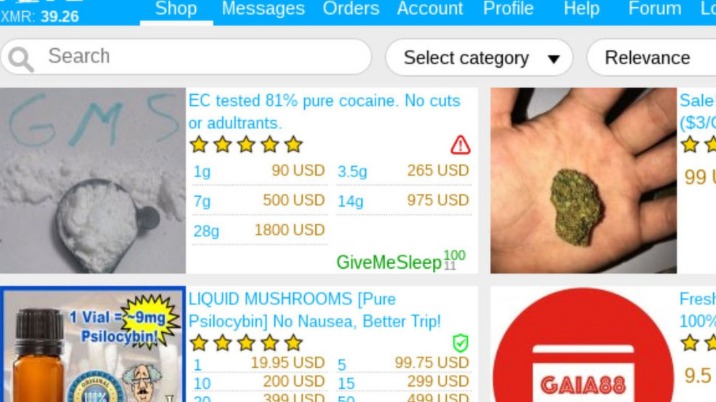
The marketplace requires merchants to pay fees to sell their products, helping ensure a certain level of quality control. Its user base is primarily English-speaking, and it appeals to more sophisticated cybercriminals. Here’s a look at the top 10 dark web markets currently dominating this underground space. Operation RapTor involves law enforcement actions taken by JCODE member agencies, including the DEA, FBI, FDA OCI, HSI, IRS-CI, and USPIS.