
Like other marketplaces, it also requires registration for new users and accepts payments in Monero. Empire Market is a dark web shop that resembles the AlphaBay marketplace. Its look, design, options, and interface are exactly the exact copy of its competitor, but everything else, including buyers, vendors, and servers, is different. At its launch, the platform accepted payments through Litecoin, but now it has incorporated support for other payment methods like Monero and Bitcoin. The platform also cares about its users and uses PGP encryption and two-factor authentication to secure their data and communication.
It also runs on the Tor network, which helps keep things anonymous. Established in 2020, Awazon Market has quickly become one of the most famous darknet marketplaces. The market claims to provide secure and anonymous commerce services. You can find a lot of goods and services packed with stealth high-level encryption, no JavaScript, and anti-DDoS protection.
Which Is The Best Laptop For Cyber Security Course?
Atlantis’s shutdown seems, judging by comments on Reddit pages & All Things Vice to have initially allowed withdrawals, but disabled it after a few days and then stole the remaining deposits+escrow+vendor-bonds. TRD denied that this was any kind of problem, so I collected order information for about a week. The arrest followed an extensive investigation by the Central Office for Combating Internet Crime (ZIT), which tracked the platform’s operations across multiple jurisdictions.
Hydra’s 2022 Collapse Led To An 894% Drop In Darknet Market Revenue
This way, it becomes very difficult to trace which websites you’re visiting, and these sites won’t know where you are located. Ethically, they must minimize harm, responsibly handle any stolen or sensitive data (often notifying victims or law enforcement), avoid entrapment, and maintain research integrity. An award-winning cybercrime threat intelligence firm, KELA’s mission is to provide 100% real, actionable intelligence on threats emerging from the cybercrime underground, to support the prevention of digital crimes. Additionally, credentials are not required to view content on this site, which is uncommon on most DNMs. Therefore, it is a good site to explore if you do not want to create credentials and/or are new to the darknet. It is usually uncommon for darknet sites to allow you to view products on their sites without eventually facing a paywall.
Darknet Threat Actors Are Not Playing Games With The Gaming Industry
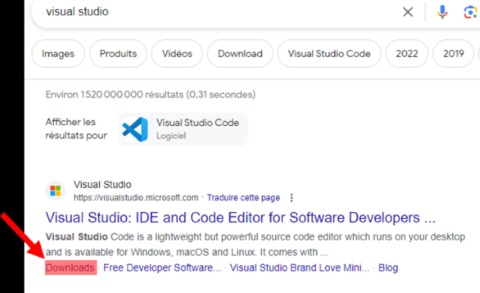
The browser uses onion routing technology to route the internet traffic through multiple relay nodes that provide layered encryption. The layers of encryption hide your data and activity from snooping eyes. Accessing darknet requires using Tor Browser, a special web browser that routes your internet traffic through a global network of relays managed by volunteers.
Best Free Firewall Software In 2025
A VPN encrypts the data traffic and keeps your activities private on the dark web. It also masks your IP address, making it difficult for government agencies to monitor or track your activities. We recommend using NordVPN as it offers top-notch security features, including dark web threat protection. At KELA, we help you identify and mitigate risks by providing actionable intelligence from the darknet.
The CSO Guide To Top Security Conferences
If you ever decide to explore the dark web, protecting your identity is crucial. Most people start by using the Tor Browser, which hides your IP address. Ransomware and cryptocurrency-based crimes saw a significant increase in 2023, with a nearly $176 million rise compared to 2022. Notably, Abacus explicitly forbids highly dangerous goods, including weapons, explosives, and exploitative material, which has helped maintain a relatively favorable reputation among its user base. Remember, staying informed is your best defense against misinformation.
Measures Against The Trade In Illegal Data
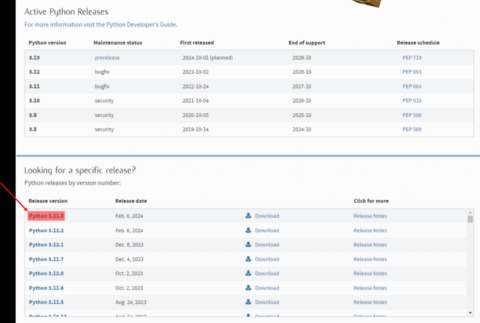
- Only two years later, his thesis project would serve as the basis for the Tor Project, a non-profit group that launched the anonymous Tor browser in 2008.
- I’ve used it a handful of times; deliveries landed smooth via DeadDrops—plain packaging, no fuss.
- Bohemia accepts Monero and Bitcoin as payment methods and places a strong emphasis on protecting user anonymity through PGP encryption.
- “Exit scams” occur when marketplace operators suddenly shut down, stealing funds from escrow wallets and disappearing.
- For instance, a recent London Metropolitan Police (MET) investigation examined the transactions of a seller profile on a DWM10.
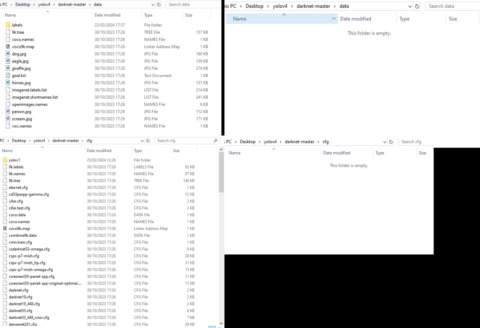
In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet. This was the initial framework for anonymous communication and file sharing. Later in 2022, the US Naval Research Laboratory built on Freenet’s idea to create a secure and encrypted network for sensitive communications, which was later released to the public as open-source software. From there, these products are then passed on to distributors, which are the dark web marketplaces in this context. On these marketplaces, they’re listed, sold, and promoted just like items on any e-commerce site.
The Dark Side Of The Internet
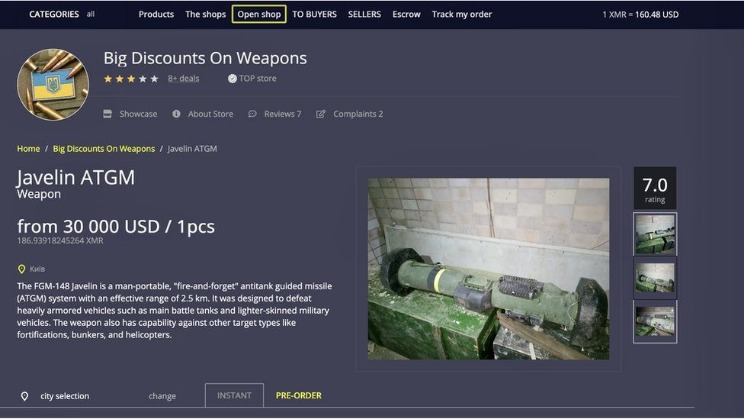
Beware of sharing your financial details on the dark web, as this can result in identity theft and your bank account amount being stolen. DarkFox Market is the largest dark web shop selling various products and attracting more vendors and users. It is a wallet-based shop, meaning you must first deposit bitcoins into your wallet before purchasing any goods and services.
How To Protect Your Identity While Browsing The Dark Web
- Finally, the growing demand for stolen data used for illegal activities such as identity theft, fraud and phishing is helping to strengthen the market.
- It scans darknet marketplaces and hacker forums to alert you instantly if anything shows up.
- Like most of the markets, STYX supports Bitcoin (BTC), Monero (XMR), and other crypto tokens to keep everyone’s identity hidden on this marketplace.
- This solution scans dark web forums to alert you if your data is being listed, traded, or otherwise exposed.
- In fact, by 2013, a Guardian article revealed that about 70% of listings were drug-related.
- The investigation revealed that Hydra had more than 19,000 sellers and a total of 17 million customers during its two years of activity.
We find that trading properties of buyers and sellers reflect the dominance of DWMs in the ecosystem. In particular, we analyse networks of ‘multihomers’, defined as users that are simultaneously trading in multiple markets. We show that these users play a crucial role in the connectivity of the ecosystem because they act as connectors between markets. Analogously, we identify and characterise ‘multisellers’ (i.e., multihomers that are sellers) and ‘multibuyers’ (i.e., multihomers that are buyers). Furthermore, we analyse the seller-to-seller (S2S) network, i.e., the network composed only of transactions among sellers, which can be regarded as a supply chain network of illicit goods and services.
While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. The only difference is that it passes your traffic through random nodes before reaching the destination. This means your activities cannot be traced or your browser history exposed. In due course, the framework was remodeled and made public as a secure browser. While it might appear tempting to venture into the dark web, it’s crucial to understand that the risks here are far more severe compared to the deep web.
Another relevant section is Cracked Accounts, where compromised user accounts for various online services are published. There is also a section called Combolists, where lists of username/password combinations are shared that can be used for credential stuffing attacks. Darknets and dark markets present a multifaceted challenge to businesses and society as a whole. While these hidden networks can be used for legitimate purposes, they are equally significant as vectors for cybercrime and illicit activities. Darknets and dark markets have fueled the growth of cybercrime, provided a marketplace for cyber threats, and expanded the attack surface for malicious actors.



